MEWBIES@: Facebook Twitter G+ YouTube DeviantArt Forum Wall
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
██ ██
█▌ - SSLv3 AND TLSv1.2 FTP SERVERS TROUBLE SHOOTING - █▌
█▌ █▌
█ ▐▌
 █ ▐▌
█ During connection to an FTP server you received errors such as sslv3 ▐▌
█ alert handshake failure, Failed TLS, gnutls_handshake: A TLS fatal, ▐▌
█ M2Crypto.SSL.SSLError, The token supplied to the function is invalid, etc. ▐▌
█ here is how to resolve it for a variety of programs. ▐▌
█ ▐▌
█ WINDOWS TOOLS SUCH AS FLASHFXP, FTPRUSH, PREEE ▐▌
█ FXP CHANGES ▐▌
█ LFTP SSLv3 CHANGES ▐▌
█ PFTP SSLv3 CHANGES ▐▌
█ EGGDROP / BOTS USING PYTHON ▐▌
█ ▐▌
█ ___________..___________ ▐▌
█ ▐▌
█ WINDOWS TOOLS SUCH AS FLASHFXP, FTPRUSH, PREEE: ▐▌
█ ``````````````````````````````````````````````` ▐▌
█ If you try to login to a server and it states: ▐▌
█ [i] Loading SSL DLL ... ▐▌
█ [i] OpenSSL 0.9.8d 28 Sep 2006 (LOCKED) ▐▌
█ [1] 234 AUTH SSL successful ▐▌
█ [1] error:14077410:SSL routines:SSL23_GET_SERVER_HELLO:sslv3 alert ▐▌
█ handshake failure ▐▌
█ [1] Network subsystem is unusable(10091) ▐▌
█ Or while transferring files: ▐▌
█ [1] 435 Failed TLS negotiation on data channel (using SSL_accept()), ▐▌
█ disconnected ▐▌
█ ▐▌
█ That is most likely because the site you are trying to login to is using ▐▌
█ SSLv3 TLSv1.2 and the client you are using to connect isn't compatible. To ▐▌
█ fix this for Windows: ▐▌
█ 1. Install Microsoft Visual C++ 2008 Redistributables. ▐▌
█ ▐▌
█ 2. Close your FTP client. Download and install the latest version of ▐▌
█ of 'Win32 OpenSSL Light' from HERE e.g. Win32OpenSSL_Light-1_0_1g.exe. ▐▌
█ (slproweb.com is endorsed by openssl.org for OpenSSL for Windows.) ▐▌
█ ▐▌
█ 3. Go to your FTP's client directory and rename (backup) libeay32.dll and ▐▌
█ ssleay32.dll to libeay32.dll-bck and ssleay32.dll-bck. ▐▌
█ ▐▌
█ 4. Copy libeay32.dll and ssleay32.dll from the newly installed ▐▌
█ OpenSSL-Win32 diretory to your FTP client's directory. ▐▌
█ ▐▌
█ Once you are connected it will now state: ▐▌
█ [i] Loading SSL DLL ... ▐▌
█ [i] OpenSSL 1.0.1e 11 Feb 2013 (LOCKED) ▐▌
█ ▐▌
█ You can delete your backed up .dll files if all is working well. ▐▌
█ ▐▌
█ NOTES: ▐▌
█ 1. Preee replace libeay32.dll and libssl32.dll. ▐▌
█ ▐▌
█ 2. IF you are using a portable packed FTPRush version that does not have ▐▌
█ libeay32.dll and ssleay32.dll in its directory - then right click on ▐▌
█ ftprush.exe and select extract to here (you'll need to have WinRar ▐▌
█ installed for that option to be on your right click menu). Then open the ▐▌
█ extracted directory and replace the dll files with the new ones. From then ▐▌
█ on use the extracted FTPRush.exe to start your FTPRush. ▐▌
█ ▐▌
█ 3. FlashFXP v3.7.7 is compatible with OpenSSL.v1.0.1e files. ▐▌
█ Earlier versions of FlashFXP might produce the error (v2.1): ▐▌
█ Failed to load SSL DLLS. ssleay32.dll or libeay32.dll ▐▌
█ ▐▌
█ 4. If you use older tools with TLSWrap and receive the error: ▐▌
█ 530 TLSWrap SSL/TLS connection to server failed; install the latest ▐▌
█ version, launch it pointing to server's cert; read here. ▐▌
█ ▐▌
█ ___________..___________ ▐▌
█ ▐▌
█ FXP CHANGES: ▐▌
█ ```````````` ▐▌
█ If you are FXP'ing from one site to another and it fails with the error: ▐▌
█ [i] Transfer Failed: f00.zip ▐▌
█ [1] 435 Failed TLS negotiation on data channel (using SSL_accept()), ▐▌
█ disconnected ▐▌
█ ▐▌
█ On the site that you are FXP'ing the files to; set it to PASV target: ▐▌
█ Using UltraFXP: ▐▌
█ Options > Site Manager > select target site > Transfer > check the box ▐▌
█ 'Use PASV When Acts as Target FXP Site(*)' ▐▌
█ Using FTPRush: ▐▌
█ Tools > Site Manager > double click target site to edit > Transfer > check ▐▌
█ the box "Use PASV when acts as target FXP Site" ▐▌
█ ▐▌
█ ▐▌
█ During connection to an FTP server you received errors such as sslv3 ▐▌
█ alert handshake failure, Failed TLS, gnutls_handshake: A TLS fatal, ▐▌
█ M2Crypto.SSL.SSLError, The token supplied to the function is invalid, etc. ▐▌
█ here is how to resolve it for a variety of programs. ▐▌
█ ▐▌
█ WINDOWS TOOLS SUCH AS FLASHFXP, FTPRUSH, PREEE ▐▌
█ FXP CHANGES ▐▌
█ LFTP SSLv3 CHANGES ▐▌
█ PFTP SSLv3 CHANGES ▐▌
█ EGGDROP / BOTS USING PYTHON ▐▌
█ ▐▌
█ ___________..___________ ▐▌
█ ▐▌
█ WINDOWS TOOLS SUCH AS FLASHFXP, FTPRUSH, PREEE: ▐▌
█ ``````````````````````````````````````````````` ▐▌
█ If you try to login to a server and it states: ▐▌
█ [i] Loading SSL DLL ... ▐▌
█ [i] OpenSSL 0.9.8d 28 Sep 2006 (LOCKED) ▐▌
█ [1] 234 AUTH SSL successful ▐▌
█ [1] error:14077410:SSL routines:SSL23_GET_SERVER_HELLO:sslv3 alert ▐▌
█ handshake failure ▐▌
█ [1] Network subsystem is unusable(10091) ▐▌
█ Or while transferring files: ▐▌
█ [1] 435 Failed TLS negotiation on data channel (using SSL_accept()), ▐▌
█ disconnected ▐▌
█ ▐▌
█ That is most likely because the site you are trying to login to is using ▐▌
█ SSLv3 TLSv1.2 and the client you are using to connect isn't compatible. To ▐▌
█ fix this for Windows: ▐▌
█ 1. Install Microsoft Visual C++ 2008 Redistributables. ▐▌
█ ▐▌
█ 2. Close your FTP client. Download and install the latest version of ▐▌
█ of 'Win32 OpenSSL Light' from HERE e.g. Win32OpenSSL_Light-1_0_1g.exe. ▐▌
█ (slproweb.com is endorsed by openssl.org for OpenSSL for Windows.) ▐▌
█ ▐▌
█ 3. Go to your FTP's client directory and rename (backup) libeay32.dll and ▐▌
█ ssleay32.dll to libeay32.dll-bck and ssleay32.dll-bck. ▐▌
█ ▐▌
█ 4. Copy libeay32.dll and ssleay32.dll from the newly installed ▐▌
█ OpenSSL-Win32 diretory to your FTP client's directory. ▐▌
█ ▐▌
█ Once you are connected it will now state: ▐▌
█ [i] Loading SSL DLL ... ▐▌
█ [i] OpenSSL 1.0.1e 11 Feb 2013 (LOCKED) ▐▌
█ ▐▌
█ You can delete your backed up .dll files if all is working well. ▐▌
█ ▐▌
█ NOTES: ▐▌
█ 1. Preee replace libeay32.dll and libssl32.dll. ▐▌
█ ▐▌
█ 2. IF you are using a portable packed FTPRush version that does not have ▐▌
█ libeay32.dll and ssleay32.dll in its directory - then right click on ▐▌
█ ftprush.exe and select extract to here (you'll need to have WinRar ▐▌
█ installed for that option to be on your right click menu). Then open the ▐▌
█ extracted directory and replace the dll files with the new ones. From then ▐▌
█ on use the extracted FTPRush.exe to start your FTPRush. ▐▌
█ ▐▌
█ 3. FlashFXP v3.7.7 is compatible with OpenSSL.v1.0.1e files. ▐▌
█ Earlier versions of FlashFXP might produce the error (v2.1): ▐▌
█ Failed to load SSL DLLS. ssleay32.dll or libeay32.dll ▐▌
█ ▐▌
█ 4. If you use older tools with TLSWrap and receive the error: ▐▌
█ 530 TLSWrap SSL/TLS connection to server failed; install the latest ▐▌
█ version, launch it pointing to server's cert; read here. ▐▌
█ ▐▌
█ ___________..___________ ▐▌
█ ▐▌
█ FXP CHANGES: ▐▌
█ ```````````` ▐▌
█ If you are FXP'ing from one site to another and it fails with the error: ▐▌
█ [i] Transfer Failed: f00.zip ▐▌
█ [1] 435 Failed TLS negotiation on data channel (using SSL_accept()), ▐▌
█ disconnected ▐▌
█ ▐▌
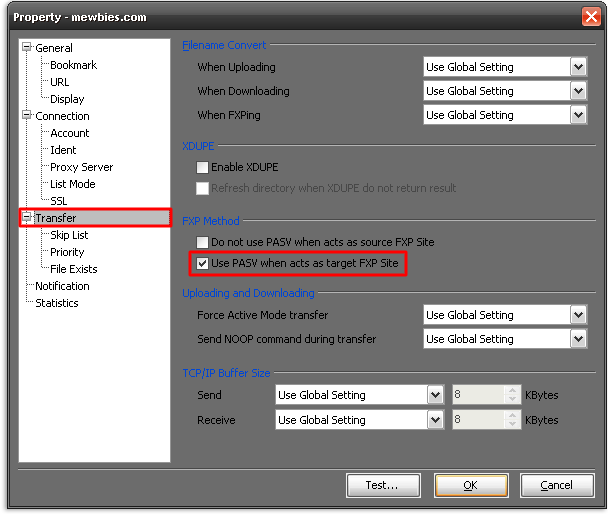
█ On the site that you are FXP'ing the files to; set it to PASV target: ▐▌
█ Using UltraFXP: ▐▌
█ Options > Site Manager > select target site > Transfer > check the box ▐▌
█ 'Use PASV When Acts as Target FXP Site(*)' ▐▌
█ Using FTPRush: ▐▌
█ Tools > Site Manager > double click target site to edit > Transfer > check ▐▌
█ the box "Use PASV when acts as target FXP Site" ▐▌
█ ▐▌
 █ ▐▌
█ ___________..___________ ▐▌
█ ▐▌
█ LFTP SSLv3 CHANGES: ▐▌
█ ``````````````````` ▐▌
█ "Fatal error: gnutls_handshake: An unexpected TLS packet was received": ▐▌
█ ▐▌
█ When connecting to a server using LFTP and the reply is: ▐▌
█ **** gnutls_handshake: A TLS fatal alert has been received. ▐▌
█ ---- Closing control socket ▐▌
█ Fatal error: gnutls_handshake: A TLS fatal alert has been received. ▐▌
█ ▐▌
█ It could mean that your LFTP wasn't compiled with OpenSSL. ▐▌
█ ▐▌
█ HOW TO VIEW IF YOUR LFTP WAS COMPILED WITH OPENSSL: ▐▌
█ To view what version you have and if compiled with OpenSSL: ▐▌
█ lftp -v ▐▌
█ Output if not, compiled with OpenSSL will state GnuTLS similar to: ▐▌
█ LFTP | Version 4.3.6 | Copyright (c) 1996-2012 Alexander V. Lukyanov ▐▌
█ [snip] ▐▌
█ Libraries used: Readline 6.2, GnuTLS 2.12.23, zlib 1.2.7 ▐▌
█ ▐▌
█ If compiled with OpenSSL will be similar to: ▐▌
█ LFTP | Version 4.4.15 | Copyright (c) 1996-2014 Alexander V. Lukyanov ▐▌
█ [snip] ▐▌
█ Libraries used: Readline 6.2, Expat 2.1.0, zlib 1.2.7 ▐▌
█ Or: ▐▌
█ Libraries used: Readline 6.2, Expat 2.1.0, OpenSSL 0.9.8o 01 Jun 2010, ▐▌
█ zlib 1.2.7 ▐▌
█ ▐▌
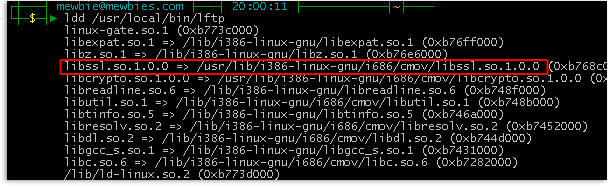
█ Another method to be sure if compiled with OpenSSL is: ▐▌
█ which lftp ▐▌
█ Output change the below path to the location of your LFTP, then: ▐▌
█ ldd /usr/bin/lftp ▐▌
█ The output will state that libssl.so as being linked: ▐▌
█ ▐▌
█ ▐▌
█ ___________..___________ ▐▌
█ ▐▌
█ LFTP SSLv3 CHANGES: ▐▌
█ ``````````````````` ▐▌
█ "Fatal error: gnutls_handshake: An unexpected TLS packet was received": ▐▌
█ ▐▌
█ When connecting to a server using LFTP and the reply is: ▐▌
█ **** gnutls_handshake: A TLS fatal alert has been received. ▐▌
█ ---- Closing control socket ▐▌
█ Fatal error: gnutls_handshake: A TLS fatal alert has been received. ▐▌
█ ▐▌
█ It could mean that your LFTP wasn't compiled with OpenSSL. ▐▌
█ ▐▌
█ HOW TO VIEW IF YOUR LFTP WAS COMPILED WITH OPENSSL: ▐▌
█ To view what version you have and if compiled with OpenSSL: ▐▌
█ lftp -v ▐▌
█ Output if not, compiled with OpenSSL will state GnuTLS similar to: ▐▌
█ LFTP | Version 4.3.6 | Copyright (c) 1996-2012 Alexander V. Lukyanov ▐▌
█ [snip] ▐▌
█ Libraries used: Readline 6.2, GnuTLS 2.12.23, zlib 1.2.7 ▐▌
█ ▐▌
█ If compiled with OpenSSL will be similar to: ▐▌
█ LFTP | Version 4.4.15 | Copyright (c) 1996-2014 Alexander V. Lukyanov ▐▌
█ [snip] ▐▌
█ Libraries used: Readline 6.2, Expat 2.1.0, zlib 1.2.7 ▐▌
█ Or: ▐▌
█ Libraries used: Readline 6.2, Expat 2.1.0, OpenSSL 0.9.8o 01 Jun 2010, ▐▌
█ zlib 1.2.7 ▐▌
█ ▐▌
█ Another method to be sure if compiled with OpenSSL is: ▐▌
█ which lftp ▐▌
█ Output change the below path to the location of your LFTP, then: ▐▌
█ ldd /usr/bin/lftp ▐▌
█ The output will state that libssl.so as being linked: ▐▌
█ ▐▌
 █ ▐▌
█ COMPILE LFTP WITH OPENSSL: ▐▌
█ Remove lftp first if you have it installed: ▐▌
█ su ▐▌
█ dpkg -r lftp ▐▌
█ aptitude update ▐▌
█ Install the dependencies you don't have: ▐▌
█ ▐▌
█ COMPILE LFTP WITH OPENSSL: ▐▌
█ Remove lftp first if you have it installed: ▐▌
█ su ▐▌
█ dpkg -r lftp ▐▌
█ aptitude update ▐▌
█ Install the dependencies you don't have: ▐▌
aptitude install openssh openssl gcc libc6 libgcc1 libgnutls26 libreadline6-dev libtinfo5 netbase
█ And for x64 install libunwind7 ▐▌
█ exit ▐▌
█ wget http://lftp.yar.ru/ftp/lftp-4.4.15.tar.gz ▐▌
█ tar xfz lftp-4.4.15.tar.gz && cd lftp-4.4.15 ▐▌
█ ./configure --with-openssl=/usr/lib ▐▌
█ Output ended with: ▐▌
█ checking for readline... configure: error: need installed readline-devel ▐▌
█ package ▐▌
█ So install whatever it states it needs, if didn't state any then skip to ▐▌
█ make: ▐▌
█ su ▐▌
█ aptitude update ▐▌
█ aptitude install libreadline6-dev ▐▌
█ exit ▐▌
█ ./configure --with-openssl=/usr/lib ▐▌
█ ▐▌
█ make ▐▌
█ I had four warnings, not to worry, only warnings: ▐▌
█ libtool: warning: ▐▌
█ '/usr/lib/gcc/i486-linux-gnu/4.7/../../../i386-linux-gnu/libexpat.la' ▐▌
█ seems to be moved ▐▌
█ ▐▌
█ Output ends with: ▐▌
█ make[1]: Leaving directory `/home/mewbies/lftp-4.4.15' ▐▌
█ ▐▌
█ su ▐▌
█ make install ▐▌
█ Output ends with: ▐▌
█ make[1]: Leaving directory `/home/mewbies/lftp-4.4.15' ▐▌
█ ▐▌
█ exit ▐▌
█ exit ▐▌
█ re-login ▐▌
█ ▐▌
█ View version again and if libssl.so is linked: ▐▌
█ lftp -v ▐▌
█ which lftp ▐▌
█ ldd /usr/local/bin/lftp ▐▌
█ Note path of lftp changed since we installed it ourself. ▐▌
█ Now it does list: ▐▌
█ libssl.so.1.0.0 = /usr/lib/i386-linux-gnu/i686/cmov/libssl.so.1.0.0 ▐▌
█ ▐▌
█ Test on a server, for example your own server if have one (add the IP to ▐▌
█ server first, i.e. site addip admin mewbies@127.0.0.1 - replace mewbies ▐▌
█ with your shell's user name): ▐▌
█ lftp ▐▌
█ open -u Name,Pass -p PORT 127.0.0.1 ▐▌
█ ls ▐▌
█ ls: ls: Fatal error: SSL_connect: self signed certificate ▐▌
█ ▐▌
█ Since I, and many, have a self signed certificate you'll receive that ▐▌
█ error. To bypass it for this sesssion only: ▐▌
█ set ssl:verif-certificate off ▐▌
█ ls ▐▌
█ bye ▐▌
█ ▐▌
█ If you want to 'set ssl:verif-certificate off' for all sites then add that ▐▌
█ line to .lftprc file with the other SSL settings: ▐▌
█ pico .lftprc ▐▌
█ For example it has this: ▐▌
█ set ftp:ssl-allow yes ▐▌
█ Change to: ▐▌
█ set ssl:verif-certificate off ▐▌
█ set ftp:ssl-allow yes ▐▌
█ ▐▌
█ Once all is working you can clean up: ▐▌
█ cd ~ ▐▌
█ rm lftp-4.4.15 -rf ▐▌
█ ▐▌
█ ___________..___________ ▐▌
█ ▐▌
█ PFTP SSLv3 CHANGES: ▐▌
█ ``````````````````` ▐▌
█ cd pftp-shit.v.1.11/src ▐▌
█ pico tlsutil.cc ▐▌
█ Ctrl + w and search for sslv3 ▐▌
█ Has this: ▐▌
█ ssl_ctx = SSL_CTX_new(SSLv3_client_method()); ▐▌
█ //ssl_ctx=SSL_CTX_new(SSLv23_client_method()); ▐▌
█ ▐▌
█ Change to: ▐▌
█ //ssl_ctx = SSL_CTX_new(SSLv23_client_method()); ▐▌
█ ssl_ctx=SSL_CTX_new(SSLv23_client_method()); ▐▌
█ ▐▌
█ ___________..___________ ▐▌
█ ▐▌
█ EGGDROP / BOTS USING PYTHON: ▐▌
█ ```````````````````````````` ▐▌
█ If your bots (eggdrop) use Python to connect to sites and receive this ▐▌
█ error when connecting to SSLv3 sites: ▐▌
█ M2Crypto.SSL.SSLError'>, SSLError('sslv3 alert handshake failure ▐▌
█ Warning, uncaught exception in <Thread(WorkerThread, started daemon ▐▌
█ -1232798864)> (<class 'M2Crypto.SSL.SSLError'> ▐▌
█ return m2.ssl_connect(self.ssl) ▐▌
█ ▐▌
█ 1. Make sure your server is up to date: ▐▌
█ su ▐▌
█ aptitude update ▐▌
█ aptitude upgrade ▐▌
█ openssl version ▐▌
█ Output similar to: ▐▌
█ OpenSSL 1.0.1e 11 Feb 2013 ▐▌
█ exit ▐▌
█ ▐▌
█ 2. Recompile the bot's script that is producing the error. For example: ▐▌
█ cd ~/bot/special/ ▐▌
█ python -m compileall ▐▌
█ ▐▌
█ ▐▌
█ //---------------------------------------------------------------------- ▐▌
█ ▐▌
█ If you find mistakes, have suggestions, and or questions please post at ▐▌
█ mewbies forum HERE - thank you. ▐▌
█ ▐▌
█ Last update on 09 Apr '14 ▐▌
█ ▐▌
█▌ █▌
█▌ - mewbies.com - █▌
█▌ █▌
██▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄██
 █ ▐▌
█ During connection to an FTP server you received errors such as sslv3 ▐▌
█ alert handshake failure, Failed TLS, gnutls_handshake: A TLS fatal, ▐▌
█ M2Crypto.SSL.SSLError, The token supplied to the function is invalid, etc. ▐▌
█ here is how to resolve it for a variety of programs. ▐▌
█ ▐▌
█ WINDOWS TOOLS SUCH AS FLASHFXP, FTPRUSH, PREEE ▐▌
█ FXP CHANGES ▐▌
█ LFTP SSLv3 CHANGES ▐▌
█ PFTP SSLv3 CHANGES ▐▌
█ EGGDROP / BOTS USING PYTHON ▐▌
█ ▐▌
█ ___________..___________ ▐▌
█ ▐▌
█ WINDOWS TOOLS SUCH AS FLASHFXP, FTPRUSH, PREEE: ▐▌
█ ``````````````````````````````````````````````` ▐▌
█ If you try to login to a server and it states: ▐▌
█ [i] Loading SSL DLL ... ▐▌
█ [i] OpenSSL 0.9.8d 28 Sep 2006 (LOCKED) ▐▌
█ [1] 234 AUTH SSL successful ▐▌
█ [1] error:14077410:SSL routines:SSL23_GET_SERVER_HELLO:sslv3 alert ▐▌
█ handshake failure ▐▌
█ [1] Network subsystem is unusable(10091) ▐▌
█ Or while transferring files: ▐▌
█ [1] 435 Failed TLS negotiation on data channel (using SSL_accept()), ▐▌
█ disconnected ▐▌
█ ▐▌
█ That is most likely because the site you are trying to login to is using ▐▌
█ SSLv3 TLSv1.2 and the client you are using to connect isn't compatible. To ▐▌
█ fix this for Windows: ▐▌
█ 1. Install Microsoft Visual C++ 2008 Redistributables. ▐▌
█ ▐▌
█ 2. Close your FTP client. Download and install the latest version of ▐▌
█ of 'Win32 OpenSSL Light' from HERE e.g. Win32OpenSSL_Light-1_0_1g.exe. ▐▌
█ (slproweb.com is endorsed by openssl.org for OpenSSL for Windows.) ▐▌
█ ▐▌
█ 3. Go to your FTP's client directory and rename (backup) libeay32.dll and ▐▌
█ ssleay32.dll to libeay32.dll-bck and ssleay32.dll-bck. ▐▌
█ ▐▌
█ 4. Copy libeay32.dll and ssleay32.dll from the newly installed ▐▌
█ OpenSSL-Win32 diretory to your FTP client's directory. ▐▌
█ ▐▌
█ Once you are connected it will now state: ▐▌
█ [i] Loading SSL DLL ... ▐▌
█ [i] OpenSSL 1.0.1e 11 Feb 2013 (LOCKED) ▐▌
█ ▐▌
█ You can delete your backed up .dll files if all is working well. ▐▌
█ ▐▌
█ NOTES: ▐▌
█ 1. Preee replace libeay32.dll and libssl32.dll. ▐▌
█ ▐▌
█ 2. IF you are using a portable packed FTPRush version that does not have ▐▌
█ libeay32.dll and ssleay32.dll in its directory - then right click on ▐▌
█ ftprush.exe and select extract to here (you'll need to have WinRar ▐▌
█ installed for that option to be on your right click menu). Then open the ▐▌
█ extracted directory and replace the dll files with the new ones. From then ▐▌
█ on use the extracted FTPRush.exe to start your FTPRush. ▐▌
█ ▐▌
█ 3. FlashFXP v3.7.7 is compatible with OpenSSL.v1.0.1e files. ▐▌
█ Earlier versions of FlashFXP might produce the error (v2.1): ▐▌
█ Failed to load SSL DLLS. ssleay32.dll or libeay32.dll ▐▌
█ ▐▌
█ 4. If you use older tools with TLSWrap and receive the error: ▐▌
█ 530 TLSWrap SSL/TLS connection to server failed; install the latest ▐▌
█ version, launch it pointing to server's cert; read here. ▐▌
█ ▐▌
█ ___________..___________ ▐▌
█ ▐▌
█ FXP CHANGES: ▐▌
█ ```````````` ▐▌
█ If you are FXP'ing from one site to another and it fails with the error: ▐▌
█ [i] Transfer Failed: f00.zip ▐▌
█ [1] 435 Failed TLS negotiation on data channel (using SSL_accept()), ▐▌
█ disconnected ▐▌
█ ▐▌
█ On the site that you are FXP'ing the files to; set it to PASV target: ▐▌
█ Using UltraFXP: ▐▌
█ Options > Site Manager > select target site > Transfer > check the box ▐▌
█ 'Use PASV When Acts as Target FXP Site(*)' ▐▌
█ Using FTPRush: ▐▌
█ Tools > Site Manager > double click target site to edit > Transfer > check ▐▌
█ the box "Use PASV when acts as target FXP Site" ▐▌
█ ▐▌
█ ▐▌
█ During connection to an FTP server you received errors such as sslv3 ▐▌
█ alert handshake failure, Failed TLS, gnutls_handshake: A TLS fatal, ▐▌
█ M2Crypto.SSL.SSLError, The token supplied to the function is invalid, etc. ▐▌
█ here is how to resolve it for a variety of programs. ▐▌
█ ▐▌
█ WINDOWS TOOLS SUCH AS FLASHFXP, FTPRUSH, PREEE ▐▌
█ FXP CHANGES ▐▌
█ LFTP SSLv3 CHANGES ▐▌
█ PFTP SSLv3 CHANGES ▐▌
█ EGGDROP / BOTS USING PYTHON ▐▌
█ ▐▌
█ ___________..___________ ▐▌
█ ▐▌
█ WINDOWS TOOLS SUCH AS FLASHFXP, FTPRUSH, PREEE: ▐▌
█ ``````````````````````````````````````````````` ▐▌
█ If you try to login to a server and it states: ▐▌
█ [i] Loading SSL DLL ... ▐▌
█ [i] OpenSSL 0.9.8d 28 Sep 2006 (LOCKED) ▐▌
█ [1] 234 AUTH SSL successful ▐▌
█ [1] error:14077410:SSL routines:SSL23_GET_SERVER_HELLO:sslv3 alert ▐▌
█ handshake failure ▐▌
█ [1] Network subsystem is unusable(10091) ▐▌
█ Or while transferring files: ▐▌
█ [1] 435 Failed TLS negotiation on data channel (using SSL_accept()), ▐▌
█ disconnected ▐▌
█ ▐▌
█ That is most likely because the site you are trying to login to is using ▐▌
█ SSLv3 TLSv1.2 and the client you are using to connect isn't compatible. To ▐▌
█ fix this for Windows: ▐▌
█ 1. Install Microsoft Visual C++ 2008 Redistributables. ▐▌
█ ▐▌
█ 2. Close your FTP client. Download and install the latest version of ▐▌
█ of 'Win32 OpenSSL Light' from HERE e.g. Win32OpenSSL_Light-1_0_1g.exe. ▐▌
█ (slproweb.com is endorsed by openssl.org for OpenSSL for Windows.) ▐▌
█ ▐▌
█ 3. Go to your FTP's client directory and rename (backup) libeay32.dll and ▐▌
█ ssleay32.dll to libeay32.dll-bck and ssleay32.dll-bck. ▐▌
█ ▐▌
█ 4. Copy libeay32.dll and ssleay32.dll from the newly installed ▐▌
█ OpenSSL-Win32 diretory to your FTP client's directory. ▐▌
█ ▐▌
█ Once you are connected it will now state: ▐▌
█ [i] Loading SSL DLL ... ▐▌
█ [i] OpenSSL 1.0.1e 11 Feb 2013 (LOCKED) ▐▌
█ ▐▌
█ You can delete your backed up .dll files if all is working well. ▐▌
█ ▐▌
█ NOTES: ▐▌
█ 1. Preee replace libeay32.dll and libssl32.dll. ▐▌
█ ▐▌
█ 2. IF you are using a portable packed FTPRush version that does not have ▐▌
█ libeay32.dll and ssleay32.dll in its directory - then right click on ▐▌
█ ftprush.exe and select extract to here (you'll need to have WinRar ▐▌
█ installed for that option to be on your right click menu). Then open the ▐▌
█ extracted directory and replace the dll files with the new ones. From then ▐▌
█ on use the extracted FTPRush.exe to start your FTPRush. ▐▌
█ ▐▌
█ 3. FlashFXP v3.7.7 is compatible with OpenSSL.v1.0.1e files. ▐▌
█ Earlier versions of FlashFXP might produce the error (v2.1): ▐▌
█ Failed to load SSL DLLS. ssleay32.dll or libeay32.dll ▐▌
█ ▐▌
█ 4. If you use older tools with TLSWrap and receive the error: ▐▌
█ 530 TLSWrap SSL/TLS connection to server failed; install the latest ▐▌
█ version, launch it pointing to server's cert; read here. ▐▌
█ ▐▌
█ ___________..___________ ▐▌
█ ▐▌
█ FXP CHANGES: ▐▌
█ ```````````` ▐▌
█ If you are FXP'ing from one site to another and it fails with the error: ▐▌
█ [i] Transfer Failed: f00.zip ▐▌
█ [1] 435 Failed TLS negotiation on data channel (using SSL_accept()), ▐▌
█ disconnected ▐▌
█ ▐▌
█ On the site that you are FXP'ing the files to; set it to PASV target: ▐▌
█ Using UltraFXP: ▐▌
█ Options > Site Manager > select target site > Transfer > check the box ▐▌
█ 'Use PASV When Acts as Target FXP Site(*)' ▐▌
█ Using FTPRush: ▐▌
█ Tools > Site Manager > double click target site to edit > Transfer > check ▐▌
█ the box "Use PASV when acts as target FXP Site" ▐▌
█ ▐▌
 █ ▐▌
█ ___________..___________ ▐▌
█ ▐▌
█ LFTP SSLv3 CHANGES: ▐▌
█ ``````````````````` ▐▌
█ "Fatal error: gnutls_handshake: An unexpected TLS packet was received": ▐▌
█ ▐▌
█ When connecting to a server using LFTP and the reply is: ▐▌
█ **** gnutls_handshake: A TLS fatal alert has been received. ▐▌
█ ---- Closing control socket ▐▌
█ Fatal error: gnutls_handshake: A TLS fatal alert has been received. ▐▌
█ ▐▌
█ It could mean that your LFTP wasn't compiled with OpenSSL. ▐▌
█ ▐▌
█ HOW TO VIEW IF YOUR LFTP WAS COMPILED WITH OPENSSL: ▐▌
█ To view what version you have and if compiled with OpenSSL: ▐▌
█ lftp -v ▐▌
█ Output if not, compiled with OpenSSL will state GnuTLS similar to: ▐▌
█ LFTP | Version 4.3.6 | Copyright (c) 1996-2012 Alexander V. Lukyanov ▐▌
█ [snip] ▐▌
█ Libraries used: Readline 6.2, GnuTLS 2.12.23, zlib 1.2.7 ▐▌
█ ▐▌
█ If compiled with OpenSSL will be similar to: ▐▌
█ LFTP | Version 4.4.15 | Copyright (c) 1996-2014 Alexander V. Lukyanov ▐▌
█ [snip] ▐▌
█ Libraries used: Readline 6.2, Expat 2.1.0, zlib 1.2.7 ▐▌
█ Or: ▐▌
█ Libraries used: Readline 6.2, Expat 2.1.0, OpenSSL 0.9.8o 01 Jun 2010, ▐▌
█ zlib 1.2.7 ▐▌
█ ▐▌
█ Another method to be sure if compiled with OpenSSL is: ▐▌
█ which lftp ▐▌
█ Output change the below path to the location of your LFTP, then: ▐▌
█ ldd /usr/bin/lftp ▐▌
█ The output will state that libssl.so as being linked: ▐▌
█ ▐▌
█ ▐▌
█ ___________..___________ ▐▌
█ ▐▌
█ LFTP SSLv3 CHANGES: ▐▌
█ ``````````````````` ▐▌
█ "Fatal error: gnutls_handshake: An unexpected TLS packet was received": ▐▌
█ ▐▌
█ When connecting to a server using LFTP and the reply is: ▐▌
█ **** gnutls_handshake: A TLS fatal alert has been received. ▐▌
█ ---- Closing control socket ▐▌
█ Fatal error: gnutls_handshake: A TLS fatal alert has been received. ▐▌
█ ▐▌
█ It could mean that your LFTP wasn't compiled with OpenSSL. ▐▌
█ ▐▌
█ HOW TO VIEW IF YOUR LFTP WAS COMPILED WITH OPENSSL: ▐▌
█ To view what version you have and if compiled with OpenSSL: ▐▌
█ lftp -v ▐▌
█ Output if not, compiled with OpenSSL will state GnuTLS similar to: ▐▌
█ LFTP | Version 4.3.6 | Copyright (c) 1996-2012 Alexander V. Lukyanov ▐▌
█ [snip] ▐▌
█ Libraries used: Readline 6.2, GnuTLS 2.12.23, zlib 1.2.7 ▐▌
█ ▐▌
█ If compiled with OpenSSL will be similar to: ▐▌
█ LFTP | Version 4.4.15 | Copyright (c) 1996-2014 Alexander V. Lukyanov ▐▌
█ [snip] ▐▌
█ Libraries used: Readline 6.2, Expat 2.1.0, zlib 1.2.7 ▐▌
█ Or: ▐▌
█ Libraries used: Readline 6.2, Expat 2.1.0, OpenSSL 0.9.8o 01 Jun 2010, ▐▌
█ zlib 1.2.7 ▐▌
█ ▐▌
█ Another method to be sure if compiled with OpenSSL is: ▐▌
█ which lftp ▐▌
█ Output change the below path to the location of your LFTP, then: ▐▌
█ ldd /usr/bin/lftp ▐▌
█ The output will state that libssl.so as being linked: ▐▌
█ ▐▌
 █ ▐▌
█ COMPILE LFTP WITH OPENSSL: ▐▌
█ Remove lftp first if you have it installed: ▐▌
█ su ▐▌
█ dpkg -r lftp ▐▌
█ aptitude update ▐▌
█ Install the dependencies you don't have: ▐▌
█ ▐▌
█ COMPILE LFTP WITH OPENSSL: ▐▌
█ Remove lftp first if you have it installed: ▐▌
█ su ▐▌
█ dpkg -r lftp ▐▌
█ aptitude update ▐▌
█ Install the dependencies you don't have: ▐▌